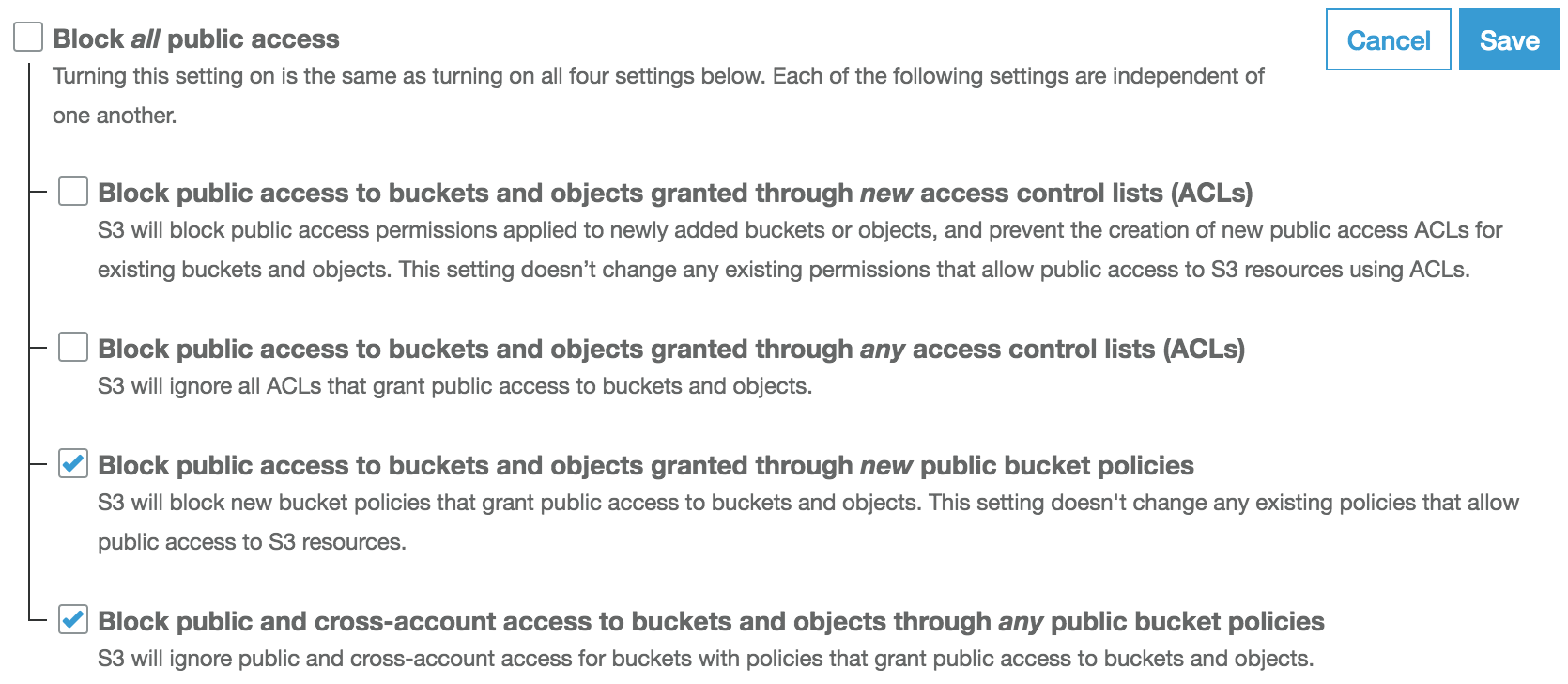
In this recipe, we learned about ACLs.
In the Granting READ ACLs for a bucket to everyone from the console section, we granted the READ permission to everyone through ACLs. In the Granting READ for AWS users using predefined groups from the CLI section, we granted the READ permission using a predefined group: AuthenticatedUsers.
The policy document for granting access through ACLs has the following structure:
{
"Grants": [
{
"Grantee": {
"DisplayName": "string",
"EmailAddress": "string",
"ID": "string",
"Type": "CanonicalUser"|"AmazonCustomerByEmail"|"Group",
"URI": "string"
},
"Permission": "FULL_CONTROL"|"WRITE"|"WRITE_ACP"|"READ"|"READ_ACP"
}
...
],
"Owner": {
"DisplayName": "string",
"ID": "string"
}
}
The grantee can be specified in one of the following ways:
- With Type as AmazonCustomerByEmail, along with the canonical ID of the account in the EmailAddress field
- With Type as CanonicalUser, along with the email for the account in the ID field
- With Type as Group, along with the URI for a predefined group in the URI field
The account can be specified using an email address or the canonical ID of the account. We can get the canonical ID of an account from the Security Credentials page of our account.
The following are globally the URIs for predefined groups and should be used in the JSON policy:
- AuthenticatedUser: http://acs.amazonaws.com/groups/global/AuthenticatedUsers
- AllUsers: http://acs.amazonaws.com/groups/global/AllUsers
- LogDelivery: http://acs.amazonaws.com/groups/s3/LogDelivery
ACLs can be used to grant the following permissions to buckets/objects:
- READ: List objects for a bucket. Read an object and its metadata.
- WRITE: Create, overwrite, or delete objects for a bucket. Not applicable for an object.
- READ_ACP: Read the ACL of a bucket or object.
- WRITE_ACP: Write the ACL for a bucket or object.
- FULL_CONTROL: All the previous permissions.
In the Granting public READ for an object with canned ACLs from the CLI section, we used a canned policy, pubic-read, which allows everyone to read that object. Canned ACLs are short-hand ACL permissions that can be used to provide permission for a resource from the command line. Currently, the following canned ACLs are supported: private, public-read, public-read-write, aws-exec-read, authenticated-read, bucket-owner-read, bucket-owner-full-control, and log-delivery-write.
In the case of cross-account access, if a user from account A uploads an object to a bucket in account B (owned by account B), account B will have no access to that object even if it is the bucket owner. Account A can, however, grant permission to the bucket owner while uploading the document using the bucket-owner-read or bucket-owner-full-control canned ACL.
We used the put-bucket-acl sub-command of the aws s3api command in this recipe to set permissions on a bucket using ACLs. Similarly, put-object-acl sets permission for an object. If we forget the policy structure for a put policy, we can execute a get policy to get the structure and modify it for our purpose. The get-bucket-acl sub-command of the aws s3api command gets the bucket's ACL policy, and get-object-policy gets an object's ACL policy.



 Free Chapter
Free Chapter