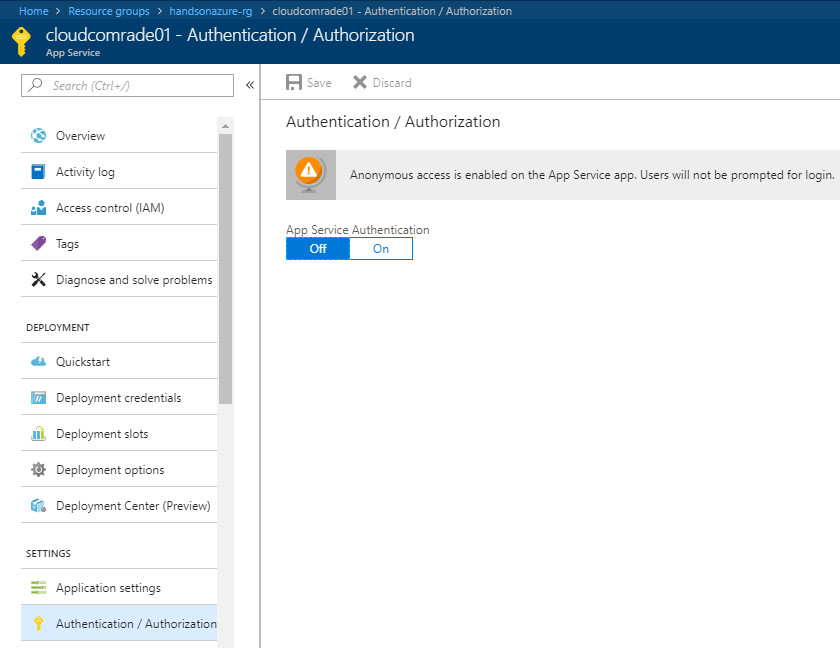
Go to your App Service and the find Authentication / Authorization blade on the left, next to Application settings as mentioned previously. When you click on it, you will see a screen for configuration:
As you can see, it is currently disabled. When you toggle the App Service Authentication feature to On, you will see new options available, with which you can configure authentication for your web app:
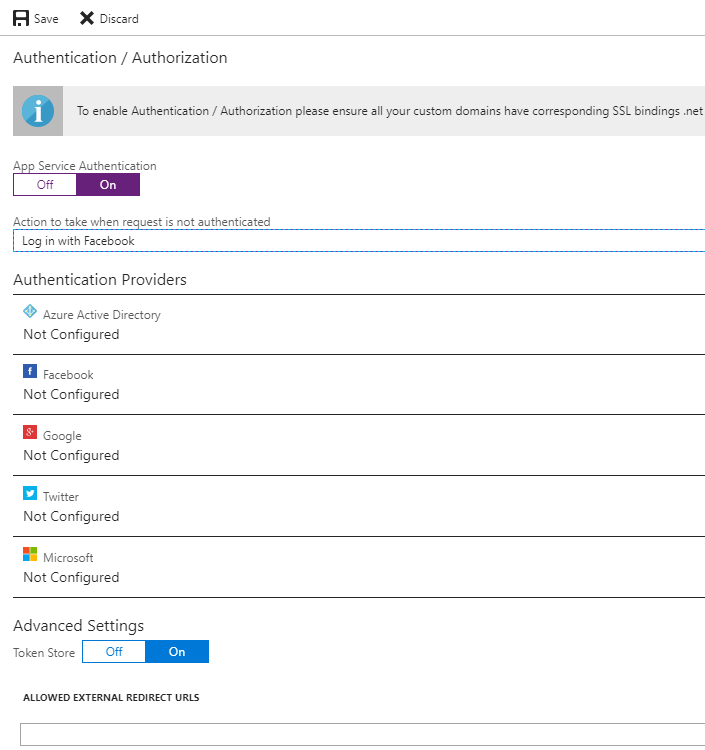
Change the Action to take when request is not authenticated field to any value available. The portal will display the following information:
To enable Authentication / Authorization please ensure all your custom domains have corresponding SSL bindings .net version is configured to "4.5" and manage pipeline mode is set to "Integrated".
Since we do not have a custom domain now, no action needs to be taken. The same applies to the .NET version and pipeline mode—if you have not changed the default parameters of your application, everything should be set correctly already. Let's now select one authentication provider and configure it—we will start with Azure Active Directory.
When you click on the Azure Active Directory option, you will see a new screen where you can configure integration. Firstly, you have to select the Management Mode:
- Off: Azure Active Directory authentication is disabled.
- Express: A quick way to configure authentication for your App Service using Azure AD. You will have to either select an already existing Azure Active Directory application or let the Azure Portal create a new one for you.
- Advanced: If Express is not enough for you, you can always enter all necessary parameters on your own. With this option, you will be able to configure integration by providing information about Client ID, Issuer URL, and optionally, Client Secret. All of these parameters can be found when browsing your Azure Active Directory application.
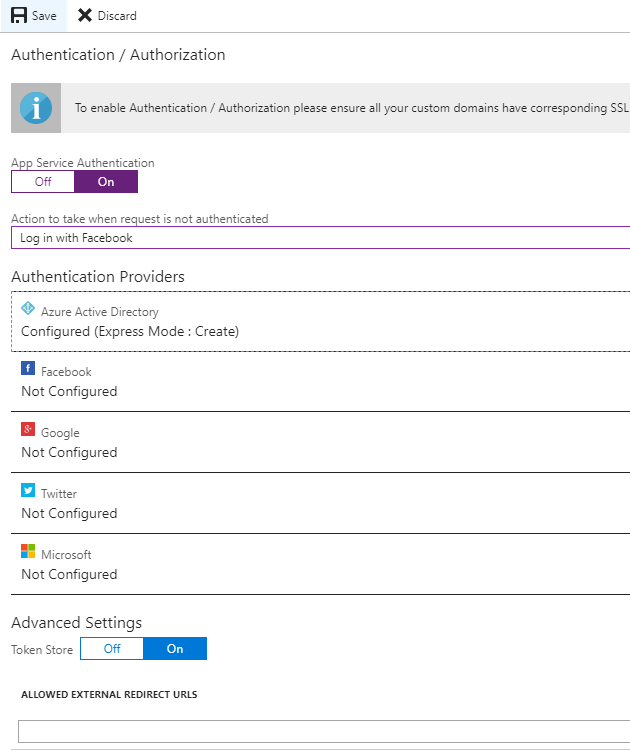
To start, I recommend using the Express option, as configuring applications in Azure Active Directory is beyond scope of this book. For now, you only need to provide a name for the application and click OK. You will go back to the previous screen, where you should be able to see that one authentication provider is already configured:
Now, let's click the Save button. After a moment, everything should be set and you can now access your application to see whether securing it works. Go to the Overview blade and click on the URL link, or enter it directly in your browser. When a default page is loaded, you will not see it, but rather will be redirected to the login page.
For this particular exercise, I have assumed that you have your application already deployed. If you have not, please go back to the previous sections and deploy your code with either Visual Studio or FTP.
Since we configured Azure Active Directory as our authentication provider, a user will be asked to give this particular application consent to access their information.



 Free Chapter
Free Chapter