Overview of this book
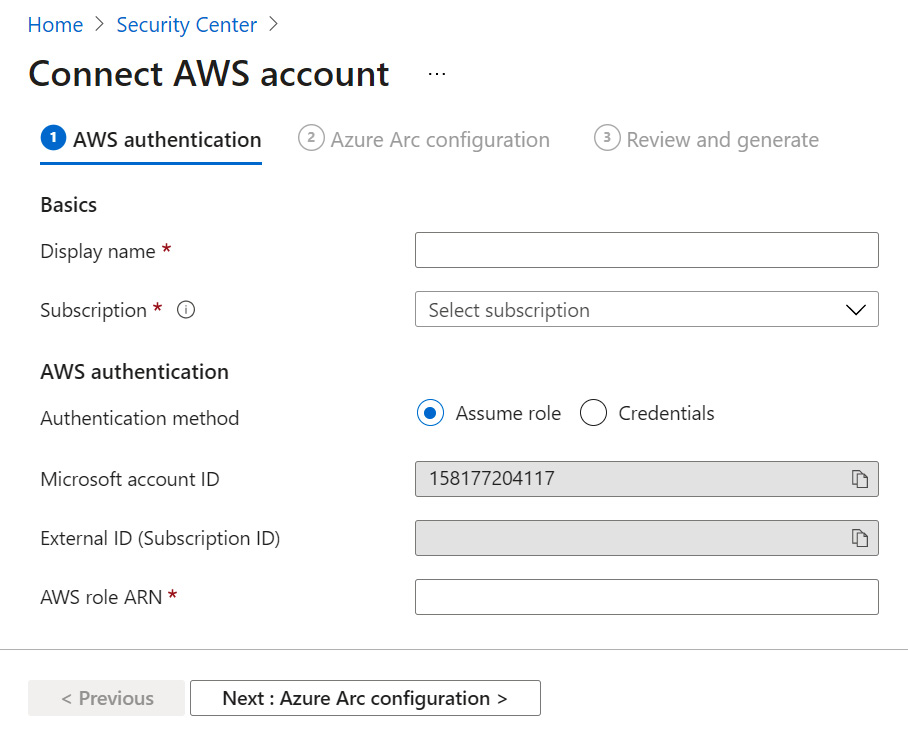
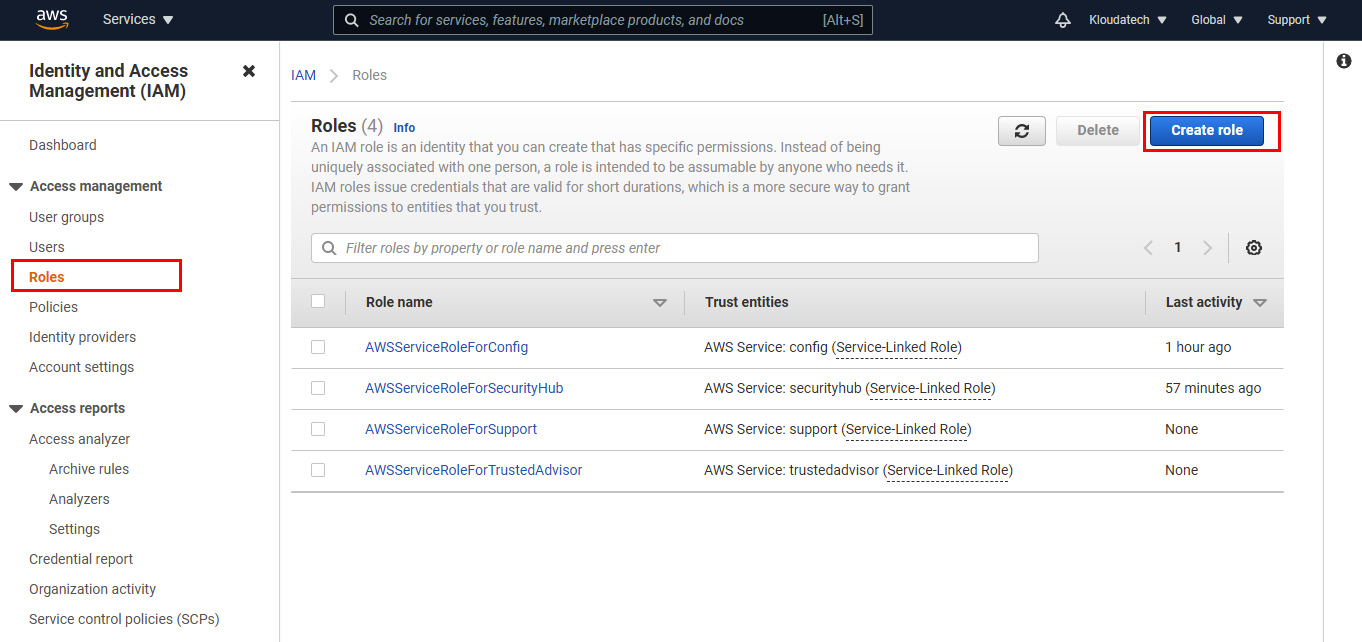
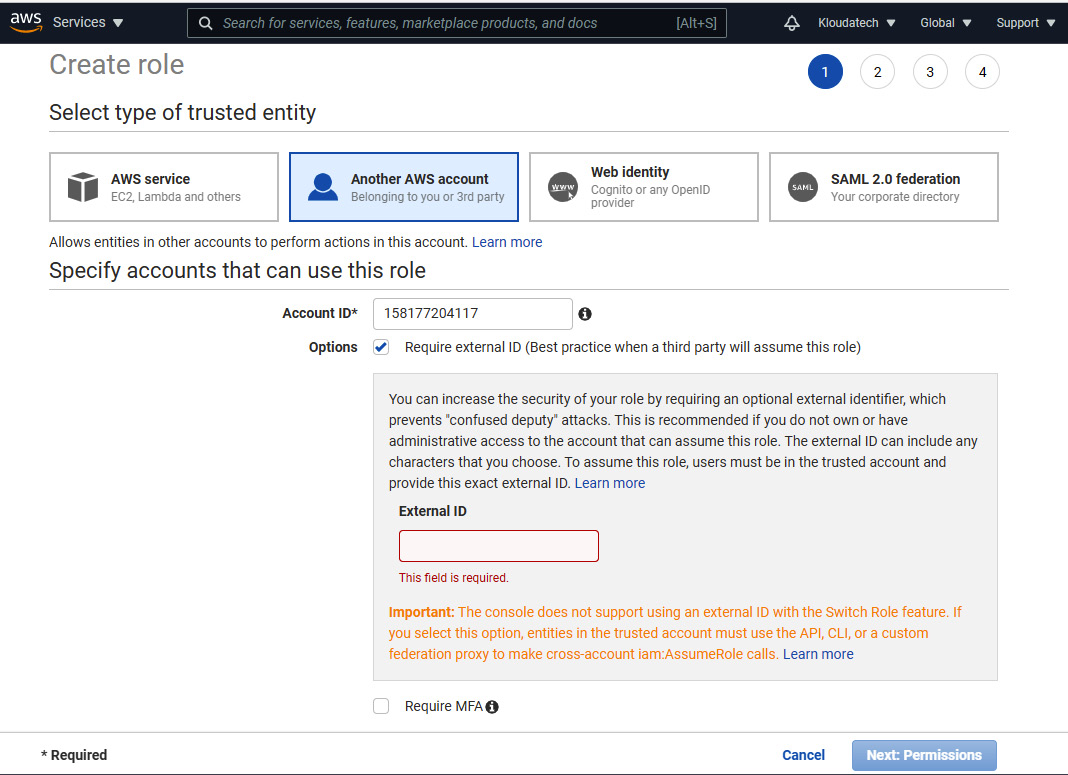
Microsoft Defender for Cloud is a multi-cloud and hybrid cloud security posture management solution that enables security administrators to build cyber defense for their Azure and non-Azure resources by providing both recommendations and security protection capabilities.
This book will start with a foundational overview of Microsoft Defender for Cloud and its core capabilities. Then, the reader is taken on a journey from enabling the service, selecting the correct tier, and configuring the data collection, to working on remediation. Next, we will continue with hands-on guidance on how to implement several security features of Microsoft Defender for Cloud, finishing with monitoring and maintenance-related topics, gaining visibility in advanced threat protection in distributed infrastructure and preventing security failures through automation.
By the end of this book, you will know how to get a view of your security posture and where to optimize security protection in your environment as well as the ins and outs of Microsoft Defender for Cloud.



 Free Chapter
Free Chapter